Everything You Need to Know About Firewalls
Firewalls, the computing kind, are named for construction firewalls that are built to provide a barrier from a fire between two structures for a limited amount of time. Computing firewalls provide a software barrier between networks managed by interfaces. An administrator can selectively allow specific types of network traffic through the firewall that’s required for business productivity and filter everything else out. In general, firewalls deny every type of traffic except for those deliberately allowed through. This is by design and is for maximum protection for internal systems and services.
Firewalls and The Need for Security
Once the public internet began, the idea of trusted networks went by way of the dinosaur. Computing professionals quickly realized that they needed some type of barrier between their network and everyone else’s network. The firewall was born of this need for more security. The concept and practical applications of modern firewalls haven’t changed much from those early days. The concept is simple but does require some illustration to understand.
The most basic firewall appliance is a computer with two network interfaces that connect two networks — typically a trusted or internal network and an untrusted or external network. The best example is where a firewall connects a small office network (Trusted) to the internet (Untrusted).
Incoming Rules
Firewalls operate by rules. There are incoming rules that direct traffic from the internet to a specific host or network segment inside a private network. An example of an incoming rule would be to allow internet users to access a product catalog that is served from a web server cluster in a DMZ. A DMZ (demilitarized zone) is a special, isolated network that is often surrounded by two firewalls — one between itself and the internet and the other is between the office/private network and itself.
Deny All
The final type of rule is the “deny all” rule that explicitly or implicitly blocks any protocol and port not explicitly allowed by other incoming or outgoing rules. It is for this reason that the deny all rule is referred to as the most important rule. The deny all rule is always the last rule to be processed in either list.
Firewall Placement
As stated previously, firewalls are logically and physically placed between networks. The firewall’s role is to filter traffic flowing between a trusted and a non-trusted network. All traffic flowing in from or out to a non-trusted network should be filtered through a firewall.
Network Firewalls vs. Host-based Firewalls
All firewalls are not created equal but all provide the same basic functionality. Firewalls are used to protect assets such as networks or data. However, host-based firewalls differ in their approaches to this solution and in their applications. Host-based firewalls protect a single asset: the host system. A host-based firewall still has incoming and outgoing rules and even a deny all master rule.
Administrators deploy and enforce rules on host-based firewalls to supplement the network firewall. If a threat enters into a network through an allowed protocol, HTTP for example, it is then the responsibility of the host-based firewall to protect individual hosts. However, it should be noted, that firewalls, both host-based and network, are but one part of an entire security strategy.
Firewalls are effective against over-the-network threats and can contain some host-based threats by not blocking protocols and ports but cannot guard against user error, negligence, or certain types of malware that require execution or user compliance. Other security layers such as disk encryption and anti-malware software are needed to prevent data loss and system compromise.
Firewall Rules and Exceptions
Firewall rules and firewall exceptions are the same technology but just different ways of looking at implementation. A firewall rule is an instruction that tells the firewall to allow or deny a particular protocol or port. An exception is an allow rule. The term “exception” means an exception to the deny all master rule.
For example, if you need to allow your customers access to an internal web service, such as a parts catalog, you would write a business justification to the networking team explaining the need for an exception to the deny all rule. The exception requires that HTTP and HTTPS traffic, destined for your parts catalog, be directed to a particular web server in your company’s DMZ.
Any exception is a potential security problem because you are allowing external, untrusted traffic into your internal network. For this reason, you should construct a DMZ to logically house systems to which untrusted traffic is bound.
The following is an example of a basic firewall rule that allows access through the firewall to an internal (DMZ) webserver:
| Interface | Source | Destination | Service | Action | Log |
| Outside | Any | 192.168.1.10 | 80,443 | Accept | Yes |
This is a simplified rule example. Rules may also include the source port, destination port, and protocol.
The following is a simplified example of a Deny All rule:
| Interface | Source | Destination | Service | Action | Log |
| Any | Any | Any | Any | Drop | Yes |
As you can see any protocol from any source to any destination for any service is dropped (ignored) and it is also logged.
Implementing IPTables
Iptables is a host-based firewall feature. Iptables is also rules-based and function based on ACCEPT, DROP, QUEUE, or RETURN. Since iptables is a host-based firewall, the rules only pertain to the host that they’re set up on and they do not affect any other host on the network.
To add rules specific to a protocol and port, add a rule that allows SSH connections.
$ sudo iptables -A INPUT -p tcp –dport 22 -j ACCEPT
This accepts all TCP connections on port 22. If you have made changes to your SSH settings to connect to a different port, change it after the –dport parameter. To allow your web server to accept connections, the rule is similar, but the port changes to 80 and 443.
$ sudo iptables -A INPUT -p tcp –dport 80 -j ACCEPT # HTTP requests
$ sudo iptables -A INPUT -p tcp –dport 443 -j ACCEPT # HTTPS requests
The above rules may be combined into a single rule.
$ sudo iptables -A INPUT -p tcp -m multiport –dports 80,443 -j ACCEPT
If your server is not going to send email, you will REJECT all outgoing traffic on port 25, which is the SMTP port.
$ sudo iptables -A OUTPUT -p tcp –dport 25 -j REJECT
Iptables are simple to implement and are very effective in preventing unwanted access to your local system.
Firewalls in Your Network
As discussed, firewalls are generally placed between a trusted network and an untrusted network but that isn’t always the case. You may place a firewall between two trusted networks. For example, you have a group of developers who want a protected network in which to test their applications. Placing a firewall between the two networks and setting up very limited access via rules is an excellent method of protecting an internal network from external traffic. Although the two networks are trusted, sometimes it is prudent to limit traffic flow into and out of certain network segments.
Firewalls for DMZs
One such segment that benefits from firewalls is the DMZ. A DMZ is a firewalled network segment that general has fewer restrictions for incoming exceptions compared to those of the internal business networks. The DMZ is logically placed outside of the corporate network but still in a firewall-protected zone. Generally, the DMZ is surrounded by at least two firewalls: One between the DMZ and the Internet and one between the internal network and the DMZ. The internal network’s internet traffic does not generally pass through the DMZ. The DMZ and the internal network share the same Internet-facing firewall.
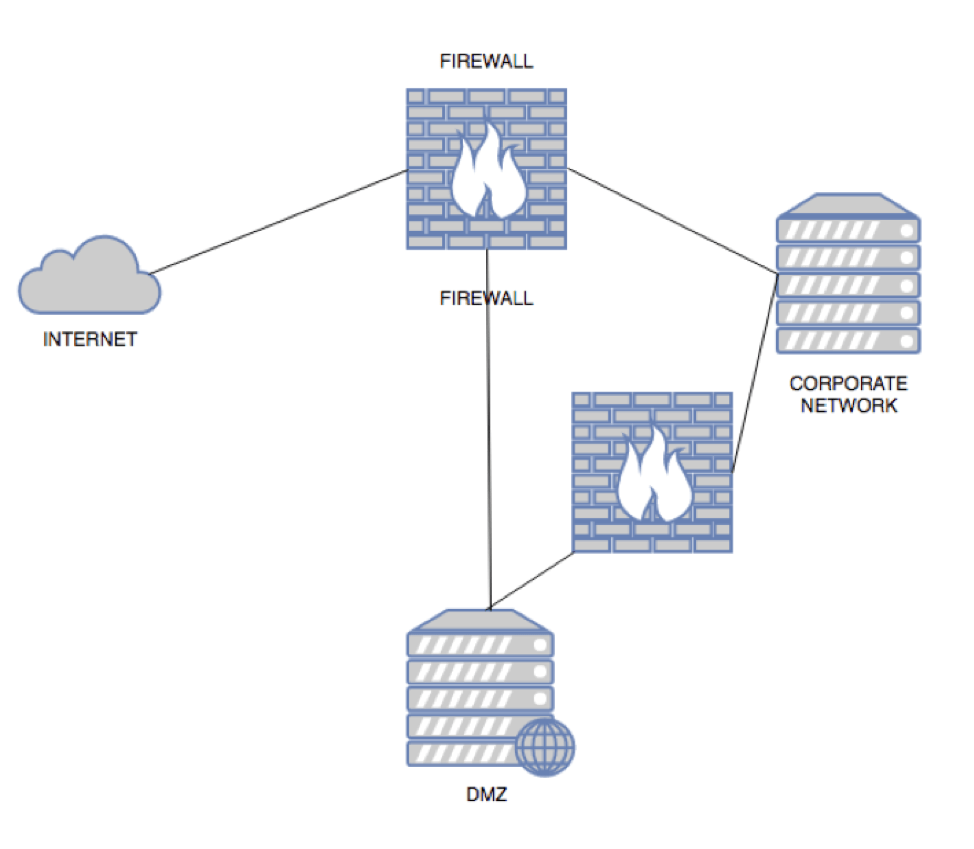
DMZ and its Connectivity between two Firewalls.
NAT and PAT
Network address translation (NAT) is commonly used to map a static public IP address to a private internal network resource as if it were directly exposed to the internet. For example, you have a website that you want to host inside your DMZ and you have setup DNS to point to a static public IP address. On your network firewall, you assign the public IP address to forward to your DMZ web server’s private or non-routed IP address. The firewall performs the translations and the webserver serves the website.
Port address translation (PAT), can be used to redirect incoming traffic on one port to use a different port after passing through the firewall. For example, your webserver in the DMZ may run its web page on port 8080, but when customers access the site they expect to access the site on port 80. Port address translation could be used to answer an incoming request on port 80, but then pass the request to the DMZ webserver on port 8080. Port address translation can also be used to run multiple pages on the same server but on different ports (ex. 8080 and 8081) but mapped on the firewall to multiple public IPs answering on port 80.
Other Firewall Types
There are other types of firewalls that don’t fall into the general definition of firewalls as compared to network or host-based firewalls but their functions and purposes are so similar that they are classified as firewalls.
Proxy Firewalls
Proxy firewalls or proxy server firewalls act as intermediaries between internal network computers and external ones such as those connected to the Internet. Unlike traditional firewalls packets don’t pass directly through a proxy. Instead, the proxy makes requests for the client computer. The purposes of a proxy are to prevent a would-be intruder from knowing which computer made a request, to provide protection through monitoring and traffic filtering, and to speed requests by caching information requested by multiple client computers. Both ends of a session (Internal computers and Internet-based computers) are conducted via the proxy so that no direct transfer of information ever occurs between the requesting client computer and an external one.
Application Firewalls
Application firewalls protect applications by denying malformed traffic that’s generally designed to disrupt applications. Application firewalls test traffic against configured policies and known vulnerabilities and then either allow or deny access to an application and its data.
Application firewalls either are active or passive in design. Active firewalls reject or allow traffic based on rules and policies, as described above. Passive firewalls act more as intrusion detection monitors in that they don’t reject or deny access but the information is logged and optionally alerted. The most common type of application firewall is the web application firewall that monitors and protects web (HTTP and HTTPS) traffic based on configured policies and rules.
Next-gen Firewalls
So-called next-generation (next-gen) firewalls combine multiple firewall technologies into one for a more comprehensive protection schema. Next-gen firewalls provides standard stateful packet inspection of a traditional firewall but adds application protection, intrusion prevention, and threat intelligence to its overall feature list.
Summary
A firewall is a set of rules and policies meant to protect systems on one side from intruders, threats, and malware from the other side. Firewalls, including Linux firewalls, are a single part of a complete security strategy. Firewalls alone do not adequately protect a network, but they can be a formidable force in preventing over-the-network attacks and threats. Companies should deploy host-based firewalls on every system inside the corporate network with a network-based firewall protecting all assets. DMZ hosts should be double firewalled and also use host-based firewalls. The types of firewalls used in a business network depend largely on the type of data and applications that require protection.
Data security is important to your business. Managing your firewall is just one portion of data security. ColoCrossing is committed to security across its colocation centers. To Get More Info, contact us and request more information.